E. Liverance, a Formula for the Root Number of a Family of Elliptic Curves
This post is the 2d in the series ECC: a gentle introduction.
In the previous mail, we have seen how elliptic curves over the existent numbers can be used to define a group. Specifically, nosotros have divers a rule for point addition: given three aligned points, their sum is zero ($P + Q + R = 0$). We have derived a geometric method and an algebraic method for computing point additions.
We then introduced scalar multiplication ($nP = P + P + \cdots + P$) and we found out an "easy" algorithm for computing scalar multiplication: double and add.
Now we will restrict our elliptic curves to finite fields, rather than the set of existent numbers, and come across how things change.
The field of integers modulo p
A finite field is, first of all, a set with a finite number of elements. An example of finite field is the set of integers modulo $p$, where $p$ is a prime number. It is more often than not denoted equally $\mathbb{Z}/p$, $GF(p)$ or $\mathbb{F}_p$. We will use the latter notation.
In fields we take 2 binary operations: addition (+) and multiplication (·). Both are airtight, associative and commutative. For both operations, there be a unique identity element, and for every chemical element in that location's a unique inverse element. Finally, multiplication is distributive over the addition: $x \cdot (y + z) = x \cdot y + x \cdot z$.
The ready of integers modulo $p$ consists of all the integers from 0 to $p - i$. Addition and multiplication work equally in modular arithmetic (too known equally "clock arithmetic"). Hither are a few examples of operations in $\mathbb{F}_{23}$:
- Addition: $(18 + 9) \bmod{23} = four$
- Subtraction: $(7 - 14) \bmod{23} = 16$
- Multiplication: $iv \cdot 7 \bmod{23} = five$
-
Condiment changed: $-5 \bmod{23} = 18$
Indeed: $(five + (-5)) \bmod{23} = (five + 18) \bmod{23} = 0$
-
Multiplicative inverse: $9^{-1} \bmod{23} = 18$
Indeed: $9 \cdot 9^{-1} \bmod{23} = nine \cdot eighteen \bmod{23} = 1$
If these equations don't look familiar to you and you demand a primer on modular arithmetics, check out Khan Academy.
Equally we already said, the integers modulo $p$ are a field, and therefore all the backdrop listed higher up hold. Note that the requirement for $p$ to be prime is important! The set of integers modulo iv is non a field: 2 has no multiplicative inverse (i.e. the equation $ii \cdot x \bmod{4} = 1$ has no solutions).
Division modulo p
We will soon define elliptic curves over $\mathbb{F}_p$, just before doing so we need a articulate thought of what $x / y$ means in $\mathbb{F}_p$. Simply put: $ten / y = ten \cdot y^{-1}$, or, in manifestly words, $x$ over $y$ is equal to $x$ times the multiplicative inverse of $y$. This fact is not surprising, simply gives us a bones method to perform sectionalisation: discover the multiplicative changed of a number and then perform a single multiplication.
Computing the multiplicative inverse can be "easily" done with the extended Euclidean algorithm, which is $O(\log p)$ (or $O(k)$ if we consider the bit length) in the worst example.
We won't enter the details of the extended Euclidean algorithm, as information technology is off-topic, however here'southward a working Python implementation:
def extended_euclidean_algorithm ( a , b ): """ Returns a three-tuple (gcd, x, y) such that a * x + b * y == gcd, where gcd is the greatest mutual divisor of a and b. This function implements the extended Euclidean algorithm and runs in O(log b) in the worst instance. """ s , old_s = 0 , 1 t , old_t = one , 0 r , old_r = b , a while r != 0 : quotient = old_r // r old_r , r = r , old_r - quotient * r old_s , s = s , old_s - quotient * south old_t , t = t , old_t - quotient * t return old_r , old_s , old_t def inverse_of ( due north , p ): """ Returns the multiplicative inverse of n modulo p. This function returns an integer m such that (due north * thousand) % p == ane. """ gcd , x , y = extended_euclidean_algorithm ( north , p ) assert ( n * x + p * y ) % p == gcd if gcd != ane : # Either northward is 0, or p is not a prime number. raise ValueError ( ' {} has no multiplicative inverse ' 'modulo {} ' . format ( n , p )) else : render x % p Elliptic curves in $\mathbb{F}_p$
At present we have all the necessary elements to restrict elliptic curves over $\mathbb{F}_p$. The set of points, that in the previous post was: $$\begin{array}{rcl} \left\{(10, y) \in \mathbb{R}^2 \correct. & \left. | \right. & \left. y^2 = x^3 + ax + b, \right. \\ & & \left. 4a^3 + 27b^ii \ne 0\right\}\ \loving cup\ \left\{0\right\} \cease{array}$$ now becomes: $$\begin{array}{rcl} \left\{(x, y) \in (\mathbb{F}_p)^two \right. & \left. | \right. & \left. y^2 \equiv x^3 + ax + b \pmod{p}, \right. \\ & & \left. 4a^three + 27b^2 \not\equiv 0 \pmod{p}\right\}\ \loving cup\ \left\{0\correct\} \end{array}$$
where 0 is still the betoken at infinity, and $a$ and $b$ are two integers in $\mathbb{F}_p$.
What previously was a continuous curve is now a set of disjoint points in the $xy$-plane. But we can testify that, even if we have restricted our domain, elliptic curves in $\mathbb{F}_p$ still form an abelian group.
Bespeak addition
Clearly, we need to alter a bit our definition of addition in order to brand it work in $\mathbb{F}_p$. With reals, nosotros said that the sum of 3 aligned points was zero ($P + Q + R = 0$). We tin go along this definition, but what does it mean for 3 points to be aligned in $\mathbb{F}_p$?
We can say that three points are aligned if at that place'southward a line that connects all of them. At present, of course, lines in $\mathbb{F}_p$ are not the same equally lines in $\mathbb{R}$. Nosotros can say, informally, that a line in $\mathbb{F}_p$ is the set of points $(x, y)$ that satisfy the equation $ax + by + c \equiv 0 \pmod{p}$ (this is the standard line equation, with the addition of "$(\text{mod}\ p)$").
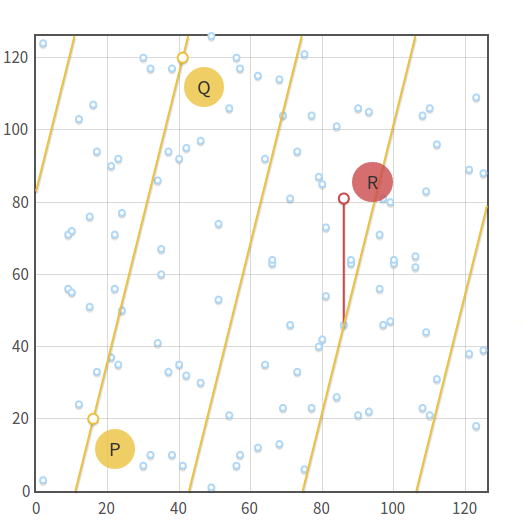
Given that we are in a group, betoken addition retains the properties we already know:
- $Q + 0 = 0 + Q = Q$ (from the definition of identity chemical element).
- Given a not-zero signal $Q$, the inverse $-Q$ is the bespeak having the same abscissa but contrary ordinate. Or, if you prefer, $-Q = (x_Q, -y_Q \bmod{p})$. For example, if a bend in $\mathbb{F}_{29}$ has a point $Q = (2, 5)$, the changed is $-Q = (2, -v \bmod{29}) = (2, 24)$.
- As well, $P + (-P) = 0$ (from the definition of inverse element).
Algebraic sum
The equations for calculating point additions are exactly the aforementioned as in the previous post, except for the fact that we need to add "$\text{mod}\ p$" at the terminate of every expression. Therefore, given $P = (x_P, y_P)$, $Q = (x_Q, y_Q)$ and $R = (x_R, y_R)$, we can calculate $P + Q = -R$ equally follows: $$\begin{align*} x_R & = (grand^2 - x_P - x_Q) \bmod{p} \\ y_R & = [y_P + m(x_R - x_P)] \bmod{p} \\ & = [y_Q + yard(x_R - x_Q)] \bmod{p} \cease{align*}$$
If $P \ne Q$, the the gradient $m$ assumes the form: $$yard = (y_P - y_Q)(x_P - x_Q)^{-ane} \bmod{p}$$
Else, if $P = Q$, we have: $$m = (three x_P^2 + a)(2 y_P)^{-1} \bmod{p}$$
It's not a coincidence that the equations take not changed: in fact, these equations work in every field, finite or infinite (with the exception of $\mathbb{F}_2$ and $\mathbb{F}_3$, which are special cased). Now I experience I have to provide a justification for this fact. The problem is: proofs for the group law generally involve circuitous mathematical concepts. Nonetheless, I plant a proof from Stefan Friedl that uses only elementary concepts. Read it if you lot are interested in why these equations work in (nigh) every field.
Back to the states — nosotros won't ascertain a geometric method: in fact, there are a few problems with that. For example, in the previous mail service, we said that to compute $P + P$ we needed to have the tangent to the curve in $P$. But without continuity, the word "tangent" does not brand any sense. Nosotros tin workaround this and other bug, however a pure geometric method would just exist too complicated and not applied at all.
Instead, you can play with the interactive tool I've written for computing point additions.
The lodge of an elliptic curve group
Nosotros said that an elliptic curve defined over a finite field has a finite number of points. An important question that nosotros need to answer is: how many points are there exactly?
Firstly, let's say that the number of points in a grouping is called the order of the group.
Trying all the possible values for $x$ from 0 to $p - ane$ is not a feasible mode to count the points, every bit it would crave $O(p)$ steps, and this is "difficult" if $p$ is a large prime number.
Luckily, in that location's a faster algorithm for calculating the order: Schoof's algorithm. I won't enter the details of the algorithm — what matters is that it runs in polynomial time, and this is what we need.
Scalar multiplication and cyclic subgroups
As with reals, multiplication can be defined as: $$due north P = \underbrace{P + P + \cdots + P}_{n\ \text{times}}$$
And, again, we can use the double and add together algorithm to perform multiplication in $O(\log north)$ steps (or $O(k)$, where $one thousand$ is the number of bits of $n$). I've written an interactive tool for scalar multiplication likewise.
Multiplication over points for elliptic curves in $\mathbb{F}_p$ has an interesting property. Take the curve $y^ii \equiv 10^3 + 2x + 3 \pmod{97}$ and the indicate $P = (iii, 6)$. Now calculate all the multiples of $P$:
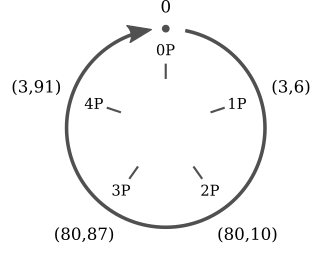
- $0P = 0$
- $1P = (3, 6)$
- $2P = (80, 10)$
- $3P = (fourscore, 87)$
- $4P = (3, 91)$
- $5P = 0$
- $6P = (3, 6)$
- $7P = (80, x)$
- $8P = (eighty, 87)$
- $9P = (iii, 91)$
- ...
Here we can immediately spot two things: firstly, the multiples of $P$ are just five: the other points of the elliptic curve never announced. Secondly, they are repeating cyclically. We tin can write:
- $5kP = 0$
- $(5k + 1)P = P$
- $(5k + 2)P = 2P$
- $(5k + 3)P = 3P$
- $(5k + 4)P = 4P$
for every integer $m$. Note that these five equations can exist "compressed" into a single one, thanks to the modulo operator: $kP = (k \bmod{five})P$.
Not merely that, but nosotros can immediately verify that these five points are closed under addition. Which ways: however I add $0$, $P$, $2P$, $3P$ or $4P$, the effect is always one of these five points. Again, the other points of the elliptic curve never appear in the results.
The aforementioned holds for every point, not merely for $P = (iii, 6)$. In fact, if we take a generic $P$: $$nP + mP = \underbrace{P + \cdots + P}_{due north\ \text{times}} + \underbrace{P + \cdots + P}_{m\ \text{times}} = (north + m)P$$
Which means: if nosotros add together two multiples of $P$, nosotros obtain a multiple of $P$ (i.eastward. multiples of $P$ are closed under addition). This is plenty to prove that the set of the multiples of $P$ is a cyclic subgroup of the group formed by the elliptic curve.
A "subgroup" is a group which is a subset of some other group. A "cyclic subgroup" is a subgroup which elements are repeating cyclically, like we have shown in the previous case. The bespeak $P$ is called generator or base indicate of the cyclic subgroup.
Cyclic subgroups are the foundations of ECC and other cryptosystems. Nosotros will run across why in the next mail service.
Subgroup order
We can ask ourselves what the society of a subgroup generated by a signal $P$ is (or, equivalently, what the order of $P$ is). To reply this question we tin can't use Schoof's algorithm, considering that algorithm only works on whole elliptic curves, not on subgroups. Before approaching the trouble, nosotros need a few more $.25:
- So far, nosotros have the defined the gild as the number of points of a group. This definition is still valid, but within a cyclic subgroup we can give a new, equivalent definition: the order of $P$ is the smallest positive integer $n$ such that $nP = 0$. In fact, if you wait at the previous case, our subgroup contained five points, and we had $5P = 0$.
- The order of $P$ is linked to the gild of the elliptic curve by Lagrange'south theorem, which states that the club of a subgroup is a divisor of the order of the parent group. In other words, if an elliptic curve contains $North$ points and one of its subgroups contains $n$ points, and so $n$ is a divisor of $N$.
These two information together give us a style to find out the social club of a subgroup with base betoken $P$:
- Calculate the elliptic curve's order $North$ using Schoof'southward algorithm.
- Find out all the divisors of $N$.
- For every divisor $n$ of $N$, compute $nP$.
- The smallest $due north$ such that $nP = 0$ is the order of the subgroup.
For example, the curve $y^2 = 10^3 - x + 3$ over the field $\mathbb{F}_{37}$ has order $North = 42$. Its subgroups may accept lodge $n = 1$, $2$, $three$, $6$, $vii$, $fourteen$, $21$ or $42$. If we try $P = (2, 3)$ we can see that $P \ne 0$, $2P \ne 0$, ..., $7P = 0$, hence the guild of $P$ is $n = seven$.
Annotation that it's of import to take the smallest divisor, not a random one. If we proceeded randomly, we could have taken $n = 14$, which is not the order of the subgroup, but 1 of its multiples.
Some other example: the elliptic curve defined past the equation $y^2 = ten^three - ten + i$ over the field $\mathbb{F}_{29}$ has guild $N = 37$, which is a prime. Its subgroups may only have guild $northward = 1$ or $37$. Equally you can easily guess, when $n = i$, the subgroup contains only the point at infinity; when $n = N$, the subgroup contains all the points of the elliptic curve.
Finding a base point
For our ECC algorithms, we want subgroups with a high order. So in full general we will choose an elliptic curve, calculate its gild ($N$), choose a high divisor as the subgroup order ($northward$) and somewhen find a suitable base point. That is: we won't choose a base point and then summate its club, but nosotros'll do the opposite: nosotros will first cull an order that looks good plenty then we will hunt for a suitable base of operations point. How do we practise that?
Firstly, nosotros need to introduce i more term. Lagrange'south theorem implies that the number $h = North / n$ is always an integer (because $n$ is a divisor of $Northward$). The number $h$ has a name: information technology'south the cofactor of the subgroup.
Now consider that for every betoken of an elliptic bend we have $NP = 0$. This happens because $N$ is a multiple of whatever candidate $n$. Using the definition of cofactor, nosotros can write: $$n(hP) = 0$$
At present suppose that $northward$ is a prime number (for reason that will be explained in the next post, we prefer prime orders). This equation, written in this grade, is telling us that the betoken $G = hP$ generates a subgroup of order $n$ (except when $G = hP = 0$, in which case the subgroup has order 1).
In the light of this, nosotros can outline the following algorithm:
- Calculate the social club $N$ of the elliptic curve.
- Choose the gild $north$ of the subgroup. For the algorithm to work, this number must be prime and must be a divisor of $N$.
- Compute the cofactor $h = Due north / northward$.
- Choose a random point $P$ on the curve.
- Compute $Chiliad = hP$.
- If $G$ is 0, and so become back to footstep 4. Otherwise nosotros accept plant a generator of a subgroup with order $north$ and cofactor $h$.
Note that this algorithm simply works if $due north$ is a prime number. If $n$ wasn't a prime, and so the lodge of $Grand$ could be one of the divisors of $n$.
Discrete logarithm
Every bit we did when working with continuous elliptic curves, we are now going to discuss the question: if we know $P$ and $Q$, what is $thou$ such that $Q = kP$?
This problem, which is known as the discrete logarithm trouble for elliptic curves, is believed to be a "difficult" problem, in that in that location is no known polynomial time algorithm that tin can run on a classical computer. In that location are, all the same, no mathematical proofs for this belief.
This problem is too analogous to the discrete logarithm trouble used with other cryptosystems such as the Digital Signature Algorithm (DSA), the Diffie-Hellman central exchange (D-H) and the ElGamal algorithm — it'south not a coincidence that they have the same name. The departure is that, with those algorithms, nosotros use modulo exponentiation instead of scalar multiplication. Their discrete logarithm problem tin be stated every bit follows: if we know $a$ and $b$, what'due south $g$ such that $b = a^thou \bmod{p}$?
Both these bug are "discrete" considering they involve finite sets (more than precisely, cyclic subgroups). And they are "logarithms" because they are analogous to ordinary logarithms.
What makes ECC interesting is that, as of today, the detached logarithm problem for elliptic curves seems to exist "harder" if compared to other similar bug used in cryptography. This implies that we need fewer bits for the integer $thou$ in order to achieve the aforementioned level of security every bit with other cryptosystems, as we will run across in details in the fourth and last post of this series.
More next week!
Enough for today! I really hope you enjoyed this mail. Go out a comment if you didn't.
Side by side week'due south mail will be the 3rd in this series and volition be about ECC algorithms: cardinal pair generation, ECDH and ECDSA. That will be one of the most interesting parts of this series. Don't miss it!
Read the next mail of the series »
Source: https://andrea.corbellini.name/2015/05/23/elliptic-curve-cryptography-finite-fields-and-discrete-logarithms/
0 Response to "E. Liverance, a Formula for the Root Number of a Family of Elliptic Curves"
Post a Comment